New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
fix(ecs): unnecessary CloudWatch logs ResourcePolicy #28495
Conversation
| this.logGroup.grantWrite(containerDefinition.taskDefinition.obtainExecutionRole()); | ||
| // These policies are required for the Execution role to use awslogs driver. | ||
| // In cases where `addToExecutionRolePolicy` is not implemented in some cases, | ||
| // for example, when used from aws-batch construct, |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
for example,
| taskDefinition: { |
…fix-ecs-log-resource-policy
…fix-ecs-log-resource-policy
| @@ -135,7 +136,16 @@ export class AwsLogDriver extends LogDriver { | |||
| ? `${this.props.maxBufferSize.toBytes({ rounding: SizeRoundingBehavior.FLOOR })}b` | |||
| : undefined; | |||
|
|
|||
| this.logGroup.grantWrite(containerDefinition.taskDefinition.obtainExecutionRole()); | |||
| // These policies are required for the Execution role to use awslogs driver. | |||
| // In cases where `addToExecutionRolePolicy` is not implemented in some cases, | |||
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
| // In cases where `addToExecutionRolePolicy` is not implemented in some cases, | |
| // In cases where `addToExecutionRolePolicy` is not implemented, |
…fix-ecs-log-resource-policy
|
@paulhcsun |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
Overall this looks good to me. Your reasoning for why resource base policy shouldn't be needed for aws log driver makes sense. I just have one concern about cases where addToPrincipalPolicy is not implemented, if that isn't an issue then I'm good to approve.
|
@paulhcsun In this case, I believe that
https://github.com/sakurai-ryo/aws-cdk/blob/10ed1948beb0f83c1b978da9c0a656aa01a382cb/packages/aws-cdk-lib/aws-iam/lib/role.ts#L521 |
|
Thanks for clarifying @sakurai-ryo, I think I just read the method names incorrectly there for
I don't see any explicit mention of that in the PR itself.
Thanks in advance for taking the time to have this discussion with me to better understand the changes. I know this is will be a big win for many people dealing with this same issue, I just want to be sure that we won't need a feature flag for it. |
|
@paulhcsun The implementation for setting IAM Policy when using AWSLogs driver was added in 2018 (#1291), while I do not think this PR breaks anything that may be a breaking change. Sorry if I misunderstood what you meant. |
|
@sakurai-ryo |
|
Thank you for contributing! Your pull request will be updated from main and then merged automatically (do not update manually, and be sure to allow changes to be pushed to your fork). |
|
Thank you for contributing! Your pull request will be updated from main and then merged automatically (do not update manually, and be sure to allow changes to be pushed to your fork). |
AWS CodeBuild CI Report
Powered by github-codebuild-logs, available on the AWS Serverless Application Repository |
|
Thank you for contributing! Your pull request will be updated from main and then merged automatically (do not update manually, and be sure to allow changes to be pushed to your fork). |
This PR modified to avoid creating unnecessary `ResourcePolicy` in CloudWatch Logs. The related issue reports an error when using the awslogs driver on ECS. This error is caused by the creation of a ResourcePolicy in CloudWatch Logs that reaches the maximum number of ResourcePolicies. https://docs.aws.amazon.com/AmazonCloudWatch/latest/logs/cloudwatch_limits_cwl.html In some cases, this ResourcePolicy will be created and in other cases it will not be created. Currently, `Grant.addToPrincipalOrResource` is used to grant permissions to ExecutionRole and Log Group in the ECS taskDef. https://github.com/aws/aws-cdk/blob/607dccb0fd920d25f0fe2613b83c9830322c439e/packages/aws-cdk-lib/aws-ecs/lib/log-drivers/aws-log-driver.ts#L138 https://github.com/aws/aws-cdk/blob/607dccb0fd920d25f0fe2613b83c9830322c439e/packages/aws-cdk-lib/aws-logs/lib/log-group.ts#L194 https://github.com/aws/aws-cdk/blob/607dccb0fd920d25f0fe2613b83c9830322c439e/packages/aws-cdk-lib/aws-iam/lib/grant.ts#L122 `Grant.addToPrincipalOrResource` first grants permissions to the Grantee (ExecutionRole) and creates a resource base policy for cross account access in cases where certain conditions are not met. This condition is determined by the contents of the `principalAccount` of the ExecutionRole and the accountID in the `env.account` and whether or not these are Tokens, but in this scenario, cross account access is not necessary. https://github.com/aws/aws-cdk/blob/607dccb0fd920d25f0fe2613b83c9830322c439e/packages/aws-cdk-lib/aws-iam/lib/grant.ts#L141 Also, when the `LogGroup.grantWrite` call was added to `aws-log-driver.ts`, the ResourcePolicy for logs could not be created from CFn and only granted to the ExecutionRole. #1291 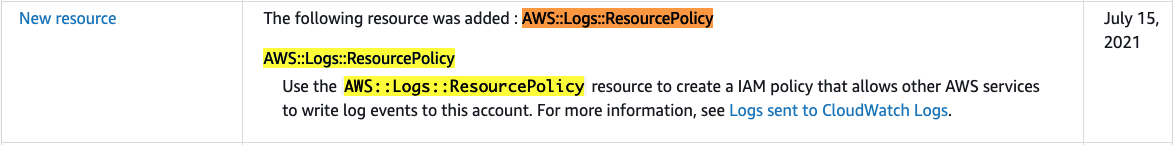 https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/ReleaseHistory.html Therefore, the resource base policy should not be necessary when using the awslogs driver. This PR changed to grant permissions only to ExecutionRole when using the awslogs driver. With this fix, ResourcePolicy will no longer be created when using the awslogs driver. I don't consider this a breaking change, as it changes the content of the generated template, but does not change the behavior of forwarding logs to CloudWatch Logs. However, if this is a breaking change, I think it is necessary to use the feature flag. fixes #22307, fixes #20313 ---- *By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license*
This PR modified to avoid creating unnecessary
ResourcePolicyin CloudWatch Logs.issue summary
The related issue reports an error when using the awslogs driver on ECS.
This error is caused by the creation of a ResourcePolicy in CloudWatch Logs that reaches the maximum number of ResourcePolicies.
https://docs.aws.amazon.com/AmazonCloudWatch/latest/logs/cloudwatch_limits_cwl.html
Current behavior
In some cases, this ResourcePolicy will be created and in other cases it will not be created.
Currently,
Grant.addToPrincipalOrResourceis used to grant permissions to ExecutionRole and Log Group in the ECS taskDef.aws-cdk/packages/aws-cdk-lib/aws-ecs/lib/log-drivers/aws-log-driver.ts
Line 138 in 607dccb
aws-cdk/packages/aws-cdk-lib/aws-logs/lib/log-group.ts
Line 194 in 607dccb
aws-cdk/packages/aws-cdk-lib/aws-iam/lib/grant.ts
Line 122 in 607dccb
Grant.addToPrincipalOrResourcefirst grants permissions to the Grantee (ExecutionRole) and creates a resource base policy for cross account access in cases where certain conditions are not met.This condition is determined by the contents of the
principalAccountof the ExecutionRole and the accountID in theenv.accountand whether or not these are Tokens, but in this scenario, cross account access is not necessary.aws-cdk/packages/aws-cdk-lib/aws-iam/lib/grant.ts
Line 141 in 607dccb
Also, when the

LogGroup.grantWritecall was added toaws-log-driver.ts, the ResourcePolicy for logs could not be created from CFn and only granted to the ExecutionRole.#1291
https://docs.aws.amazon.com/AWSCloudFormation/latest/UserGuide/ReleaseHistory.html
Therefore, the resource base policy should not be necessary when using the awslogs driver.
Major changes
This PR changed to grant permissions only to ExecutionRole when using the awslogs driver.
With this fix, ResourcePolicy will no longer be created when using the awslogs driver.
I don't consider this a breaking change, as it changes the content of the generated template, but does not change the behavior of forwarding logs to CloudWatch Logs.
However, if this is a breaking change, I think it is necessary to use the feature flag.
fixes #22307, fixes #20313
By submitting this pull request, I confirm that my contribution is made under the terms of the Apache-2.0 license