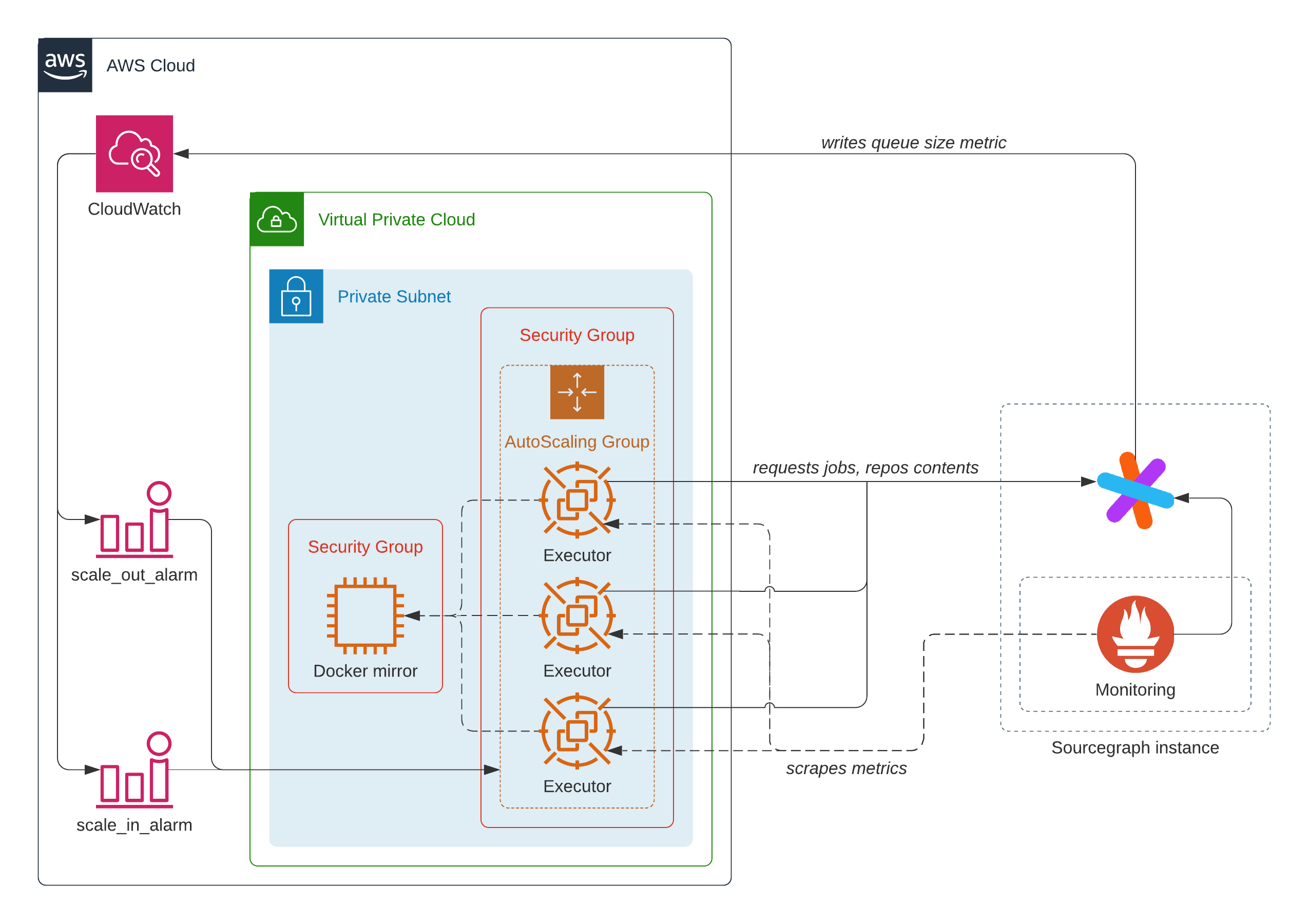
This repository provides a Terraform module to provision Sourcegraph executor compute resources on AWS. If you are installing executors for the first time, follow our complete setup guide.
This repository provides four submodules:
- The executors module provisions compute resources for executors.
- The docker-mirror module provisions a Docker registry pull-through cache.
- The networking module provisions a network to be shared by the executor and Docker registry resources.
- The credentials module provisions credentials required by the Sourcegraph instance to enable observability and auto-scaling of executors.
The multiple-executors example uses the submodule directly to provision multiple executor resource groups performing different types of work. Follow this example if you are:
- Provisioning executors for use with multiple features (e.g., both auto-indexing and server-side batch changes), or
- Provisioning resources for multiple Sourcegraph instances (e.g., test, prod)
This repository also provides a root module combining the executors, network, and docker-mirror resources into an easier to use package.
The single-executor example uses the root module to provision a single executor type. Follow this example if you are deploying to a single Sourcegraph instance and using a single executors-backed feature.
- Terraform
- 4.1.0 and below:
~> 1.1.0 - 4.2.0 and above:
>= 1.1.0, < 2.0.0
- 4.1.0 and below:
- hashicorp/aws
- 4.1.0 and below:
~> 3.0.0 - 4.2.0 and above:
>= 3.0, < 5.3.0
- 4.1.0 and below:
Please follow our setup guide on how to deploy executors using Terraform.
By default, the Terraform module will create two security groups. One for the Docker Mirror and the other for
the Launch Template. To provide a custom security group instead, set the variable security_group_id with
the ID of the security group.
If a custom security group is provided, the following rules need to be set
- Allows ingress access on the specified SSH CIDR range (defaults to
10.0.0.0/16) - Allows ingress access to the Docker Registry on the specified HTTP CIDR range (defaults to
10.0.0.0/16) - Allows all outgoing network traffic
An example iam-policy.json is provided to demonstrate the minimal permissions required to deploy and destroy an executor Terraform module. Replace all instances of AWS_ACCOUNT_ID in the JSON file with the account ID you wish to deploy your executors into.
The major and minor versions both need to match the Sourcegraph version the executors are talking to. Patch version don't need to match and it's generally advised to use the latest available. For example:
| Sourcegraph version | Terraform module version |
|---|---|
| 3.37.0 | 3.37.* |
| 3.37.3 | 3.37.* |
| 3.38.0 | 3.38.* |