New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
gosec: G104 -> ignoring functions doesn't work for types containing .
#3749
Comments
|
Hey, thank you for opening your first Issue ! 🙂 If you would like to contribute we have a guide for contributors. |
|
Hello, it's a problem related to YAML and Viper: In YAML, to use linters-settings:
gosec:
includes:
- G104
config:
G104:
fmt:
- Fscanf
"net.Conn":
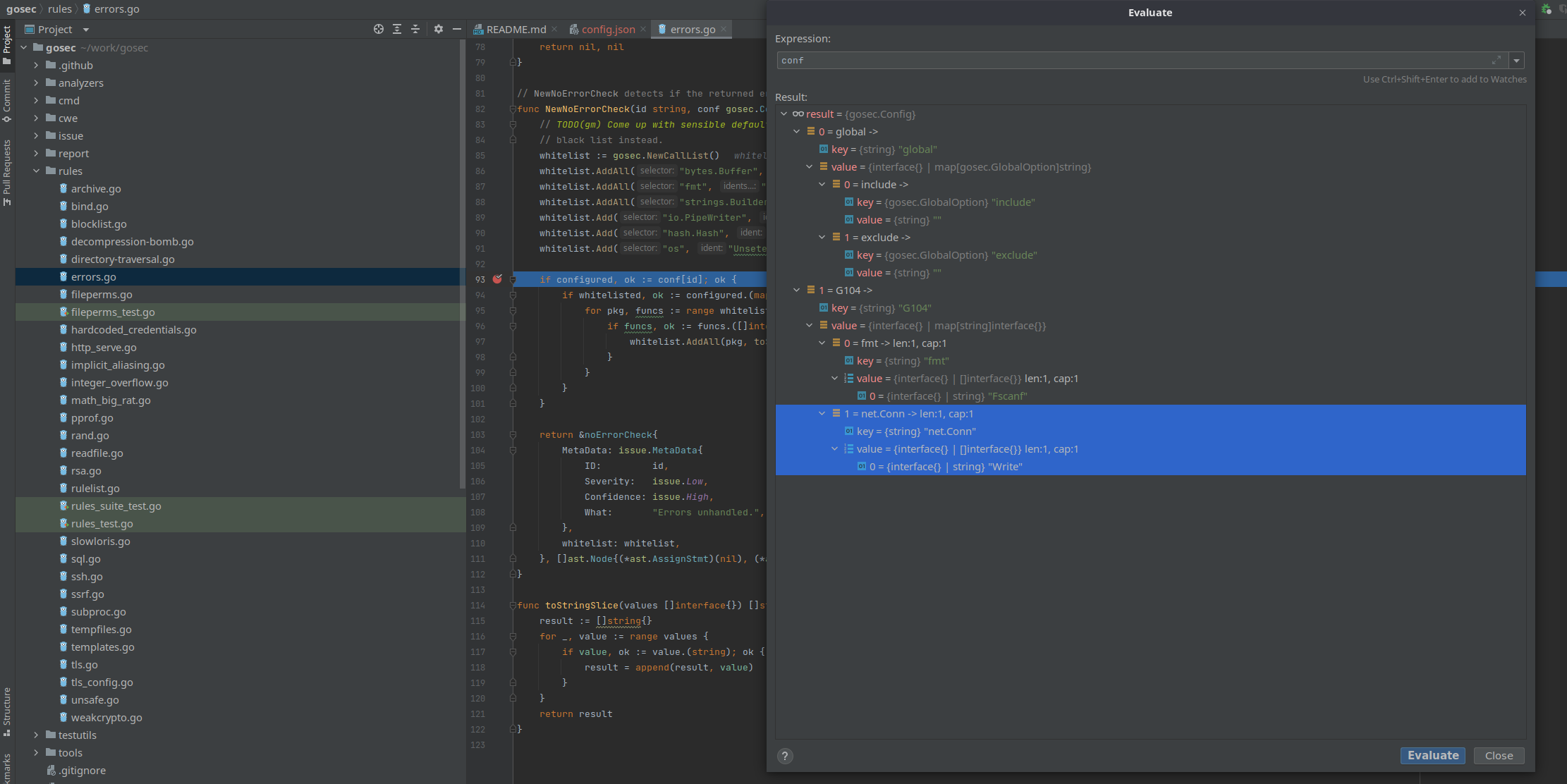
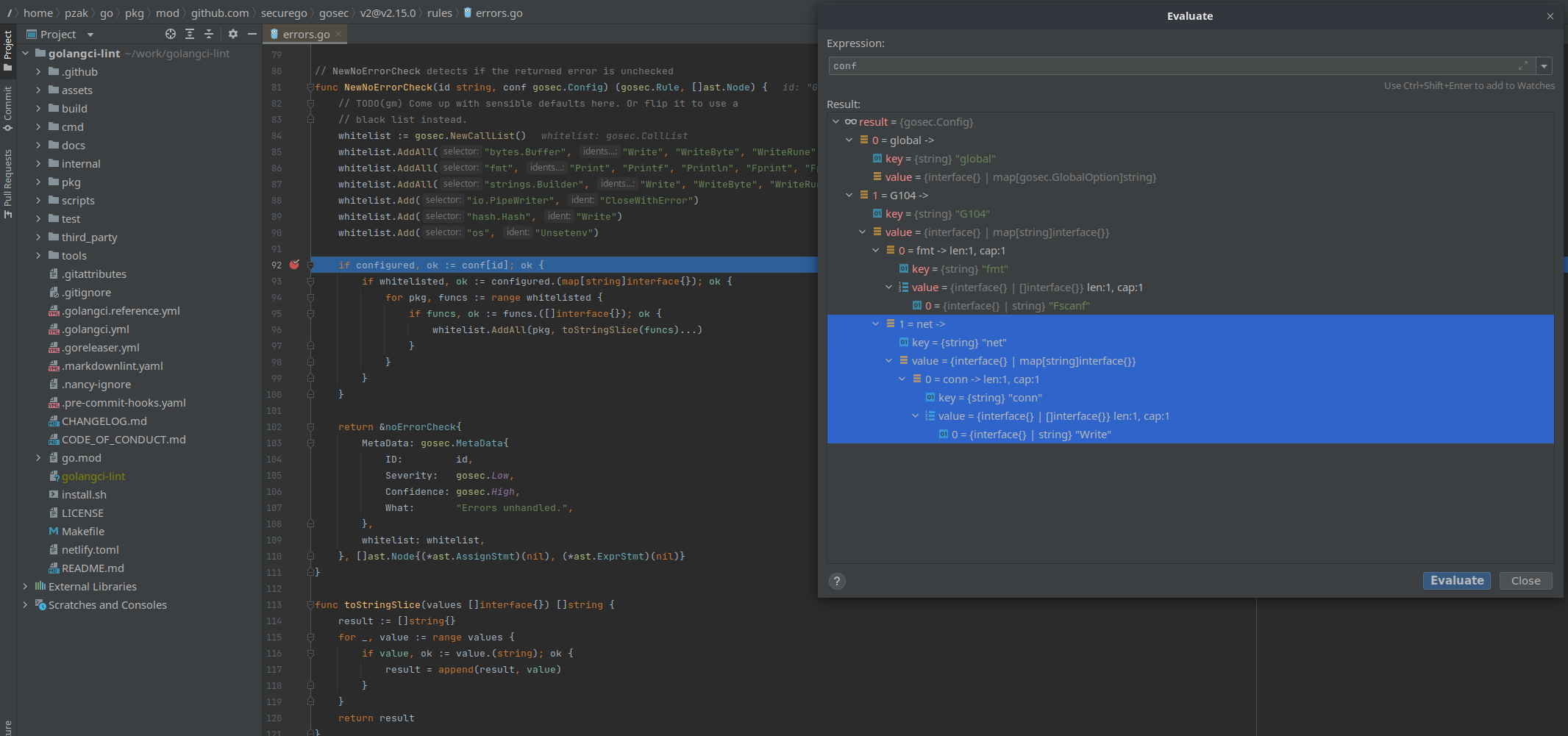
- WriteBut the way that viper read YAML doesn't follow the YAML spec, at the end you have something like that: {"G104":{"fmt":["Fscanf"],"net":{"conn":["Write"]}},"global":{}}Unfortunately, this parsing cannot be controlled only for a field in Viper. |
|
Read my message #3749 (comment) |
Might it be "corrected" in |
|
Not really because it is not just an "expanded" parsing but there is also a modification of the case. Another example to illustrate the problem: linters:
disable-all: true
enable:
- gosec
linters-settings:
gosec:
includes:
- G104
config:
G104:
fmt:
- Fscanf
"net.FooBar":
- Write
issues:
exclude-use-default: false{"G104":{"fmt":["Fscanf"],"net":{"foobar":["Write"]}},"global":{}}So it's impossible to "correct" that. |
|
AFAIU, changing config type to
{
"linters": {
"disable-all": true,
"enable": [
"gosec"
]
},
"linters-settings": {
"gosec": {
"includes": [
"G104"
],
"config": {
"G104": {
"fmt": [
"Fscanf"
],
"net.Conn": [
"Write"
]
}
}
}
},
"issues": {
"exclude-use-default": false
}
}or
[linters]
disable-all = true
enable = [ "gosec" ]
[linters-settings.gosec]
includes = [ "G104" ]
[linters-settings.gosec.config.G104]
fmt = [ "Fscanf" ]
"net.Conn" = [ "Write" ]
[issues]
exclude-use-default = false |
|
@ldez would it be acceptable to change the viper key delimiter in the config to something else, like "::"? If this has happened twice already, I see it happening again with another linter down the road. |
|
@nickajacks1 I already tried that and this creates regressions on other elements, so it's not acceptable. |
|
Do you recall what broke when you changed the delimiter? I don't see |
Welcome
Description of the problem
I can ignore
fmt.Fscanfbut ignoringnet.Conn.Writedoesn't work.When I run gosec directly with the following configuration:
{ "G104": { "fmt": ["Fscanf"], "net.Conn": ["Write"] } }I get no issues found:
Version of golangci-lint
Configuration file
Go environment
Verbose output of running
Code example or link to a public repository
The text was updated successfully, but these errors were encountered: