-
Notifications
You must be signed in to change notification settings - Fork 95
Fix incorrect vulnerable manifest path check #186
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Fix incorrect vulnerable manifest path check #186
Conversation
|
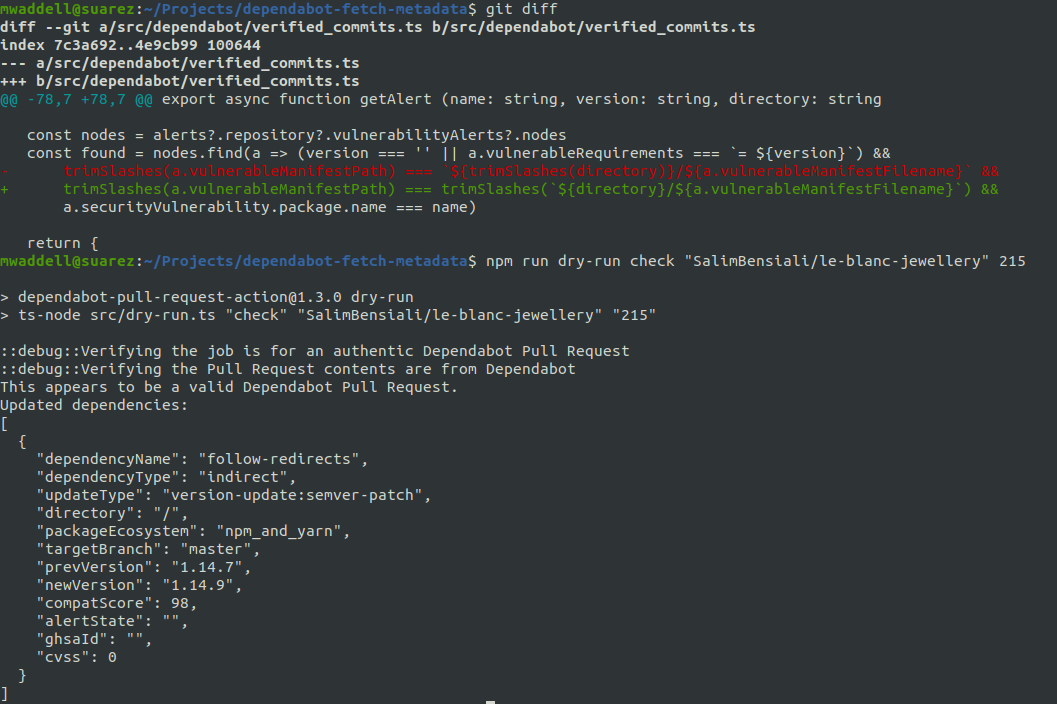
@SalimBensiali I don't believe that this PR addresses the issue you reported: |
|
This b31caa4 does expose a bug in how |
|
|
||
| const nodes = alerts?.repository?.vulnerabilityAlerts?.nodes | ||
| const found = nodes.find(a => (version === '' || a.vulnerableRequirements === `= ${version}`) && | ||
| trimSlashes(a.vulnerableManifestPath) === `${trimSlashes(directory)}/${a.vulnerableManifestFilename}` && |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@mwaddell without the propsed change, when package.json is at root, you get the following:
a.vulnerableManifestPathequals/package.jsonwhich makestrimSlashes(a.vulnerableManifestPath)resolve topackage.json`${trimSlashes(directory)}/${a.vulnerableManifestFilename}`is equivalent to`${trimSlashes('/')}/package.json`which yields/package.json
And so basically the slash trimmed paths never match, ending up making getAlert never return a matching security alert
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
I understand now - thank you for the clarification
|
@mwaddell I will run the dry-run command to verify on my end |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@brrygrdn please merge
|
Thanks for this @SalimBensiali - it looks like the |
Head branch was pushed to by a user without write access
|
Done ✅ |
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
🚀
Closes #185