____ ______ ______ ____ __ __ ____
/ || || || \| |__| || \
| o || || || o ) | | || _ |
| ||_| |_||_| |_|| _/| | | || | |
| _ | | | | | | | | ` ' || | |
| | | | | | | | | \ / | | |
|__|__| |__| |__| |__| \_/\_/ |__|__|
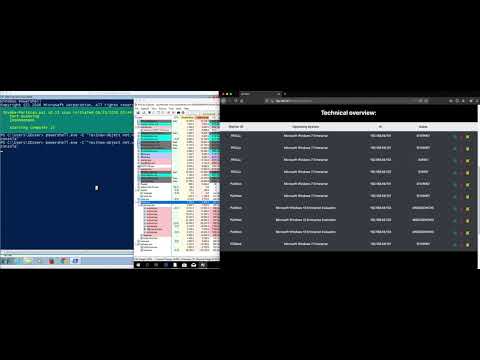
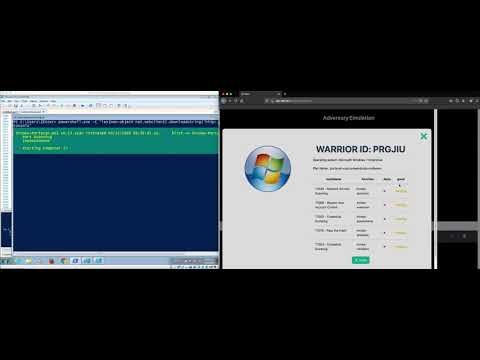
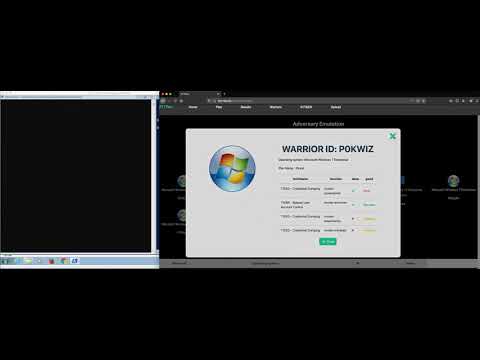
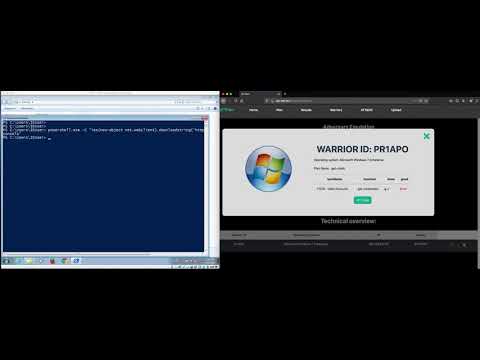
ATTPwn is a computer security tool designed to emulate adversaries. The tool aims to bring emulation of a real threat into closer contact with implementations based on the techniques and tactics from the MITRE ATT&CK framework. The goal is to simulate how a threat works in an intrusion scenario, where the threat has been successfully deployed. It is focused on Microsoft Windows systems through the use of the Powershell command line. This enables the different techniques based on MITRE ATT&CK to be applied. ATTPwn is designed to allow the emulation of adversaries as for a Red Team exercise and to verify the effectiveness and efficiency of the organization's controls in the face of a real threat.
To run ATTPwn it is mandatory to have PowerShell 3.0 or higher. To run the ATTPwn you need python 3 or higher and some python libraries. You can install this with:
pip install -r requirements.txt
Note: ATTPwn works in python 3.X. Make sure you run a pip relative to this version.
python app.py
Now, open your browser: http://localhost:5000
user: root
pass: toor
You can use:
docker build -t attpwn:latest .
You can create a container:
docker run --rm -d -p 5000:5000 attpwn:latest
ATTPwn - All-in-One: Discovery + privilege escalation + credential dumping + lateral movement on W10
ATTPwn: Generation of a basic threat plan and deployment on machine to check your controls/defenses)
This project is licensed under the GNU General Public License - see the LICENSE file for details
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. WHENEVER YOU MAKE A CONTRIBUTION TO A REPOSITORY CONTAINING NOTICE OF A LICENSE, YOU LICENSE YOUR CONTRIBUTION UNDER THE SAME TERMS, AND YOU AGREE THAT YOU HAVE THE RIGHT TO LICENSE YOUR CONTRIBUTION UNDER THOSE TERMS. IF YOU HAVE A SEPARATE AGREEMENT TO LICENSE YOUR CONTRIBUTIONS UNDER DIFFERENT TERMS, SUCH AS A CONTRIBUTOR LICENSE AGREEMENT, THAT AGREEMENT WILL SUPERSEDE.
This software doesn't have a QA Process. This software is a Proof of Concept.
If you have any problems, you can contact: