shellcode_hashs was created inspired by a script of the same name in flare.
Find the name that matches the hash used in the shellcode.
Use the database created by flare script.
Since Ghidra could not import sqlite, I created a script to convert it to json.
Convert with the following command:
python sqlite2json.py
Open the target shellcode and execute the script.
Finds XOR instructions whose source and destination operands are not equivalent.
It is registered in the bookmark.
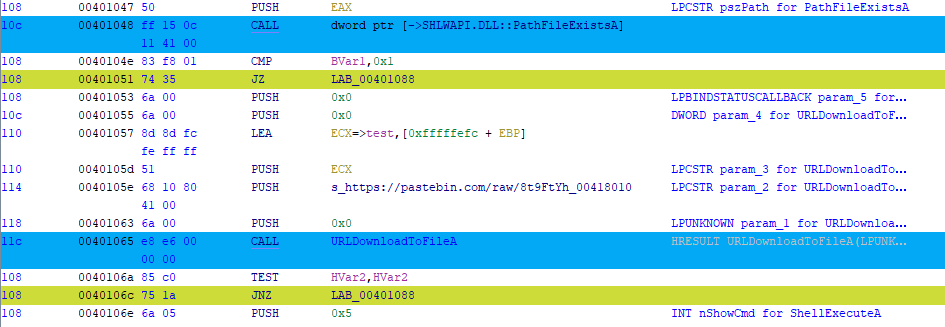
Coloring of CALL and JMP instructions.
Color the following instructions
- CALL
- JE
- JZ
- JNE
- JNZ
- JA
- JAE
- JBE
- JB
- JL
- JLE
- JG
- JGE
Deobfuscate stackstrings used by Godzilla Loader.