New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
XSS in tagify's template wrapper #988
Comments
|
Hi rrott, thank you for the detailed analysis Why is this a Tagify issue? It's up the the developer which uses Tagify to sanitize the content before saving it in the database. front-end code assumes all content sent from the app's API (and from DB to API) has already been verified before it was saved to the DB. |
|
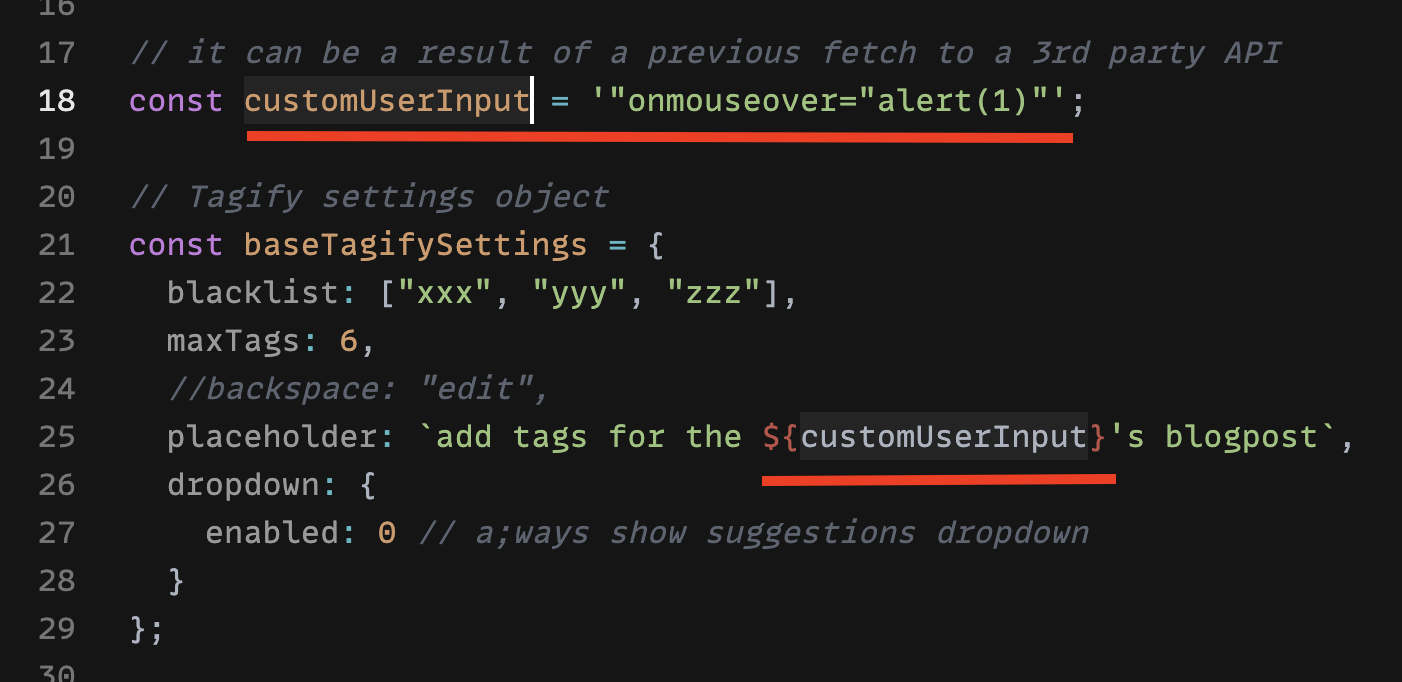
It is highly unlikely a developer will write javascript, intentionally, within the If a developer writes this, then he/she did this on purpose with full knowledge what will happen. Also, there are custom templates which a developer might use, so by your logic, the developer can also add any javascript there as well, so adding stuff to the HTML can happen in several places where the developer has control over, for example: let tagify = new Tagify(inputElm, {
placeholder: 'x "onmouseover=\"alert(1)\""',
templates: {
tag(tagData, tagify){
var _s = this.settings;
return `<tag title="${(tagData.title || tagData.value)}"
contenteditable='false'
spellcheck='false'
tabIndex="${_s.a11y.focusableTags ? 0 : -1}"
class="${_s.classNames.tag} ${tagData.class || ""}"
${this.getAttributes(tagData)}>
<x title='' class="${_s.classNames.tagX}" role='button' aria-label='remove tag'></x>
<div onmouseover=\"alert(1)\">
123
</div>
</tag>`
},
},Can you please tell me how would such malicious code might gets to those settings without a developer intentionally wrote it? |
|
I've created the PR 989, which uses your internal helper, designed precisely for that purpose.
I cannot understand why you tend to reject it? Here is an example of such a typical behavior: tagify-react-wrapper-forked All the breaches, hacks, and data losses result from somebody's mistake. Many developers use StackOverflow, copy-paste code, skip testing, etc., etc. None is perfect - even Tagify has a bug and unexpected behavior.
No, the logic is: developers do not expect Tagify to parse and render XSS payloads. It is undocumented and dangerous behavior. |
|
I've seen your PR and the fix was done in the wrong place, since many developers are using custom templates, which your fix does not address.
Because I do not agree with your level of panic and I believe none of what you've said will ever happen. I just don't understand what do you get from all this and why are you doing all this? what is you agenda? |
|
Check my acc to see that you are wrong. I saw this bug in the wild, in a real project. The issue's root was in Tagify, so PR was sent to improve it. It's open-source, is not it? I came up with a bug report and a solution; nobody blames the lib. Let's discuss the PR. I am unfamiliar with Tagify's codebase, and I can be wrong. |
|
I've implemented your suggestion, but in a better way, and will push the fix soon |
Prerequisites
💥 Demo Page
React issue template:
tagify-react-wrapper-forked
Explanation
We have found a bug in tagify's template wrapper that leads to XSS vulnerability, making applications that use
tagify.jsorreact.tagifyvulnerable as well.An attacker can use XSS to send a malicious script to an unsuspecting user. The end user's browser has no way to know that the script should not be trusted and will execute the script. Because it thinks the script came from a trusted source, the malicious script can access any cookies, session tokens, or other sensitive information retained by the browser and used with that site. These scripts can even rewrite the content of the HTML page.
Refs:
https://owasp.org/www-community/attacks/xss/
https://cheatsheetseries.owasp.org/cheatsheets/Cross_Site_Scripting_Prevention_Cheat_Sheet.html
Affected file:
https://github.com/yairEO/tagify/blob/master/src/parts/templates.js#L13
Example on codesandbox.io
Steps to reproduce:
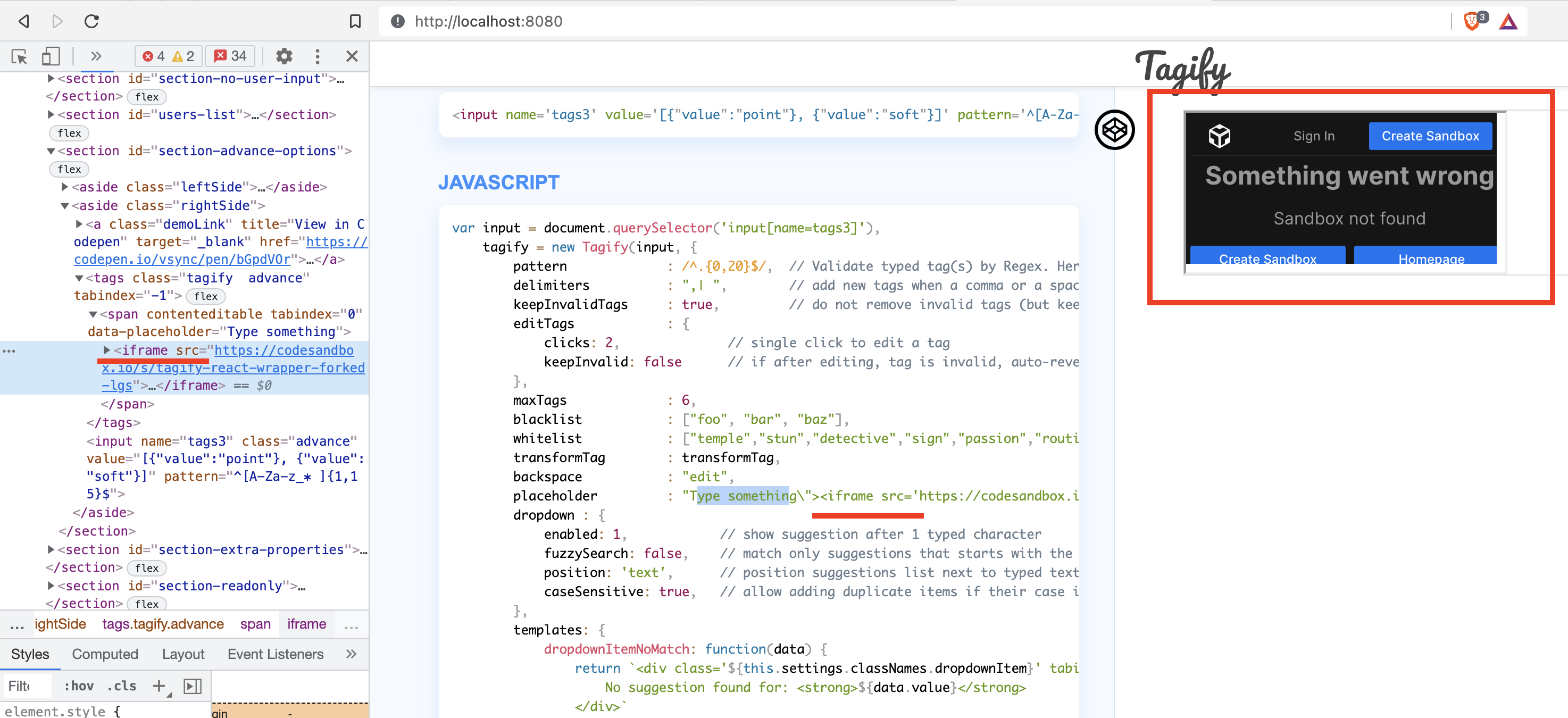
customUserInputvariable is declared. This variable mocks data that came from an API or an input.customUserInputvariable to customize tags.The following screenshot shows the XSS run on codesandbox.io

The following screenshot shows the same XSS run in the dev build of the app.

As you see, the tagify builds a new span with an attribute that was not supposed to be there.
The text was updated successfully, but these errors were encountered: