New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Release 4.3.7 - Release Candidate 1 - E2E UX tests - Vulnerability Detector #14683
Comments
General Setting in the manager
|
Fresh Install: Patch the vulnerable package to force a "solved" alert. 🟢Patch the vulnerable package to force a "solved" alert. 🟢Amazon Linux
CentosUbuntuWindowsArch LinuxUninstall the vulnerable package to force a "solved" alert. 🟢Amazon LinuxCentOSUbuntuWindows
|
Upgrade 4.3.6 to 4.3.7: Patch the vulnerable package to force a "solved" alert. 🟢Upgrade Section
Centos - Patch the vulnerable package to force a "solved" alert. |
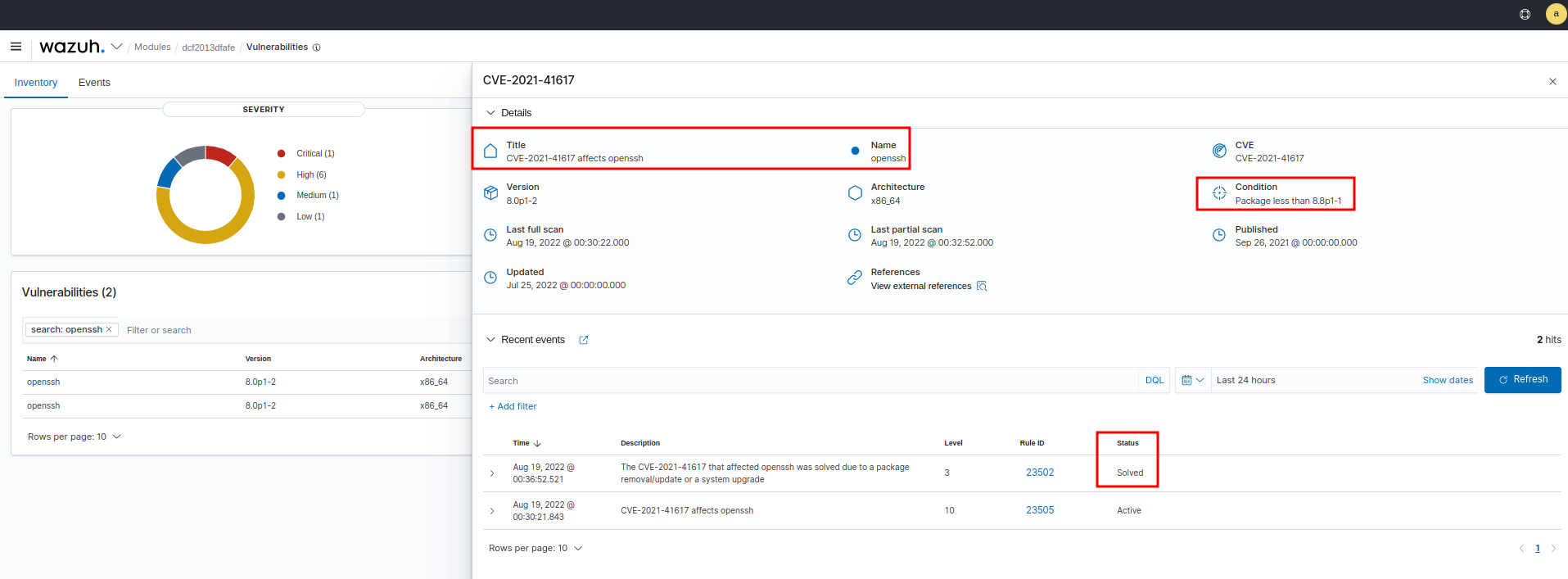
ConclusionAfter testing the cases, we can visualize the generated and resolved alerts with the UI. |
|
The tests look good but the flow was:
In the real world, a user fixes the vulnerable package (like curl) but the Wazuh agent is not restarted. I understand that the restart was performed in order to force the vulnerability scan, but I'm not sure if we are missing something due to this restart. @vikman90 what do you think? do we need to add at least a test without restarting the agent? should we repeat all the tests? |
|
Hi @jesuslinares, IMO we should approve this test as it has been executed like the previous one (wazuh/wazuh-qa#3106). We will extend this case in future releases. |



































Description
The following issue aims to run the specified test for the current release candidate, report the results, and open new issues for any encountered errors.
Test information
Tasks
Fresh Install: Patch the vulnerable package to force a "solved" alert.
Upgrade 4.3.6 to 4.3.7: Patch the vulnerable package to force a "solved" alert.
References
Conclusions 🟢
Auditors' validation
The definition of done for this one is the validation of the conclusions and the test results from all auditors.
All checks from below must be accepted in order to close this issue.
The text was updated successfully, but these errors were encountered: