New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Add JUnit-XML format report #1453
Add JUnit-XML format report #1453
Conversation
2bbded8
to
00f3daa
Compare
There was a problem hiding this comment.
Choose a reason for hiding this comment
The reason will be displayed to describe this comment to others. Learn more.
@naokikimura Awesome, thank you! 😎
This format should also be added to Brakeman.get_formats_from_output_format so one can specify -o report.junit. I recognize there are way too much code to touch for adding a new report format, my apologies.
Have you been able to validate the output? I tried your report against a random online validator against this schema and got the following issues:
- Cvc-complex-type.2.4.a: Invalid Content Was Found Starting With Element 'brakeman:properties'. One Of '{testsuite}' Is Expected., Line '2', Column '43'.
- Cvc-pattern-valid: Value '2020-02-05T20:34:51+09:00' Is Not Facet-valid With Respect To Pattern '[0-9]{4}-[0-9]{2}-[0-9]{2}T[0-9]{2}:[0-9]{2}:[0-9]{2}' For Type 'ISO8601_DATETIME_PATTERN'., Line '19', Column '201'.
- Cvc-attribute.3: The Value '2020-02-05T20:34:51+09:00' Of Attribute 'timestamp' On Element 'testsuite' Is Not Valid With Respect To Its Type, 'ISO8601_DATETIME_PATTERN'., Line '19', Column '201'.
- Cvc-complex-type.2.4.a: Invalid Content Was Found Starting With Element 'testcase'. One Of '{properties}' Is Expected., Line '20', Column '88'.
However, you need to remove the `brakeman` namespace.
|
@presidentbeef Thank you for reviewing. There are several variations of the JUnit-XML schema, and other reporters(eg ESLint) are often not compliant.
JUnit-XML is less expressive, so I added Brakeman-specific information using namespaces. In most cases, elements and attributes added using namespaces are ignored and have no effect on existing systems that handle JUnit-XML. If you want to get XML compliant with JUnit.xsd, remove the elements and attributes belonging to the It's easy with XMLStarlet. brakeman -f junit | xmlstarlet ed -d '//brakeman:*' -d '//@brakeman:*' > report-junit.xml |
|
@naokikimura Do you happen to have a public CircleCI build where I can see the results? Have you tested it yourself on CircleCI? Just want some assurance before I merge 😀 |
@presidentbeef Here is the result of scanning https://app.circleci.com/jobs/github/naokikimura/brakeman/12/tests |
|
Thank you so much for your work on adding this report format! 🙇 |
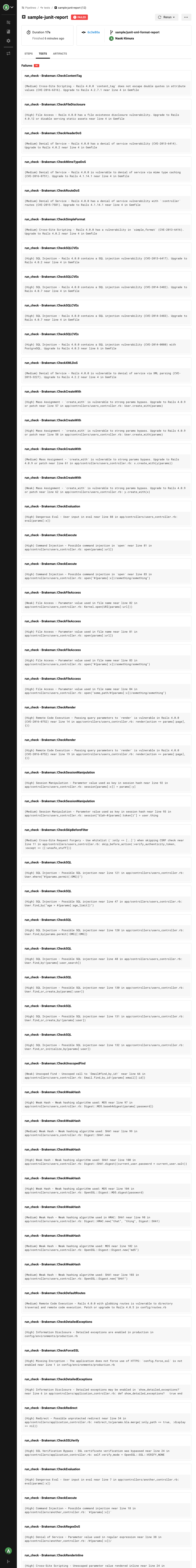
I want to gain insight into Brakeman's results at CircleCI. Therefore, JUnit-XML format report is required.
Reference: Collecting Test Metadata - CircleCI
The result of
./bin/brakeman -f junit ./test/apps/rails6is:If you remove the elements and attributes that belong to the brakeman namespace, you will get a valid XML in JUnit.xsd as follows: