New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Implement KeyObject (node:crypto)
#2036
Comments
|
Any updates? This blocks |
|
I believe this is also blocking all Firebase projects at the moment :( |
|
|
|
What needs to be done for this to get fixed? This has been broken since Feb of this year lol. |
|
Digging into this a little I found that the existing node crypto is implemented here. Looking at the code in node for crypto it looks like the web standard class Would this be a sane approach? |
|
@gingermusketeer I feel like the better option would be to migrate away from crypto-browserify and simply re export everything in node:crypto until Bun can natively support those APIs. If I understand the purpose of node-fallbacks it's to provide wrappers for default node APIs where bun doesn't have support (please correct me if I am I in err) |
@ehuff700 how would this work? I don't think node:crypto is accessible from bun. |
|
It also blocks passport-magic-login |
|
I figured I might as well link to the source, the screenshot in the report is referencing this line in jsonwebtoken (https://github.com/auth0/node-jsonwebtoken/blob/master/sign.js#L114), which is the same reson I landed here. There is also an issue on jsonwebtoken pertaining to compatability with bun: auth0/node-jsonwebtoken#939 |
|
Waiting for this |
|
Waiting too |
|
Waiting too. I came because of jsonwebtoken module |
|
I answered here and it may help you: |
|
Same issue here from my Nestjs app err: {
"type": "Error",
"message": "\u001b[38;5;3m[GlobalExceptionFilter] \u001b[39m\u001b[35mGET: \u001b[0m\u001b[31mRight hand side of instanceof is not an object\u001b[39m\n{\n \"domain\": \"\",\n \"identifier\": \"/accounts/me\"\n}",
"stack":
TypeError: Right hand side of instanceof is not an object
at /Users/myuser/Projects/nestjs/api/node_modules/jsonwebtoken/verify.js:120:10
at getSecret (/Users/myuser/Projects/nestjs/api/node_modules/jsonwebtoken/verify.js:96:51)
at /Users/myuser/Projects/nestjs/api/node_modules/jsonwebtoken/verify.js:101:7
at /Users/myuser/Projects/nestjs/api/node_modules/passport-jwt/lib/verify_jwt.js:3:59
at /Users/myuser/Projects/nestjs/api/node_modules/passport-jwt/lib/strategy.js:104:16
at /Users/myuser/Projects/nestjs/api/node_modules/passport-jwt/lib/strategy.js:39:42
at /Users/myuser/Projects/nestjs/api/node_modules/passport-jwt/lib/strategy.js:99:8
at attempt (/Users/myuser/Projects/nestjs/api/node_modules/passport/lib/middleware/authenticate.js:369:8)
at authenticate (/Users/myuser/Projects/nestjs/api/node_modules/passport/lib/middleware/authenticate.js:369:8)
at /Users/myuser/Projects/nestjs/api/node_modules/@nestjs/passport/dist/auth.guard.js:95:63
at new Promise (:1:21)
at /Users/myuser/Projects/nestjs/api/node_modules/@nestjs/passport/dist/auth.guard.js:88:8
at /Users/myuser/Projects/nestjs/api/node_modules/@nestjs/passport/dist/auth.guard.js:49:24
at fulfilled (/Users/myuser/Projects/nestjs/api/node_modules/@nestjs/passport/dist/auth.guard.js:16:68)
at processTicksAndRejections (:55:77)
}Is there an estimated date for the fix? I just wanna know when to continue with the migration from Node to Bun. |
|
and i am done already from bun sadly :') , No firebase bun need sponsores and more contributions :') , had to go back to node & pnpm |
The PNPM/package manager side of bun should still work well! |
|
Hi, I have the same issue using NestJS, It was working with node before migrating to bun. I ran "bun i @nestjs/jwt@9.0.0" an it worked! I believe it might work for most of the previous issues related to nestjs commented too. Also I needed to downgrade passwort-jwt with "bun i passport-jwt@4.0.0" Hope this comment helps. Thank you :) |
|
any news here? Im facing the same issue with bun and jsonwebtoken :c |
It worked, thank you |
|
It worked for me as well!! |
|
False :/ , I just realized that I ran the wrong command: "start:dev": "NODE_ENV=localdev nest start --watch \"bun run\"",It was missing the --exec flag . It seems the problem comes from |
|
I'm using jose with Elysia and is working well for me `import * as jose from 'jose'; const secret = new TextEncoder().encode('123456...EXAMPLE') export const sign = async (payload: any, expiration: string) => { }; export const verify = async (token: any) => { } export const jwtMiddleware = async (req: any) => { }` |
|
Switched to a different jwt library: https://www.npmjs.com/package/njwt |
It seem to be a good solution too. The problem is that some important dependencies use jsonwebtoken in the background like "@nest/jsonwebtoken", "passport-jwt", "firebase-admin", "express-jwt" which impacts some projects. |
|
Exactly. I am using passport in one of my projects and I had to use a custom strategy using jose instead of passport-jwt. |
Yea, even njwt borked for me on build. Jose seems to work for now. |
|
bun sucks.Errors everywhere bcrypto not working jwt and even spinning multiple a cluster |
|
@tonyea did you use passport-jwt in your project? I used TypeError: Right hand side of instanceof is not an object
at <anonymous> (/Users/mikaelboutin/Desktop/coding/bun-backend/node_modules/jsonwebtoken/verify.js:120:10)
at getSecret (/Users/mikaelboutin/Desktop/coding/bun-backend/node_modules/jsonwebtoken/verify.js:96:51)
at <anonymous> (/Users/mikaelboutin/Desktop/coding/bun-backend/node_modules/jsonwebtoken/verify.js:101:7)
at <anonymous> (/Users/mikaelboutin/Desktop/coding/bun-backend/node_modules/passport-jwt/lib/verify_jwt.js:3:59)
at <anonymous> (/Users/mikaelboutin/Desktop/coding/bun-backend/node_modules/passport-jwt/lib/strategy.js:104:20)
at <anonymous> (/Users/mikaelboutin/Desktop/coding/bun-backend/node_modules/passport-jwt/lib/strategy.js:39:42)
at <anonymous> (/Users/mikaelboutin/Desktop/coding/bun-backend/node_modules/passport-jwt/lib/strategy.js:99:12)
at attempt (/Users/mikaelboutin/Desktop/coding/bun-backend/node_modules/passport/lib/middleware/authenticate.js:369:8)
at authenticate (/Users/mikaelboutin/Desktop/coding/bun-backend/node_modules/passport/lib/middleware/authenticate.js:369:8)
... |
Do you mind sharing this? working on my own right now |
Sorry no, didn't use passport so wouldn't have good advice |
Downgrading jwt to 8.5.1 worked for me, just as @AlexRoosWork replied on that issue |
|
Upgraded to bun 1.06 and it seems to be solved 🎉 ref #5940 |
This blocks the popular
jsonwebtokenmodule.From Discord:
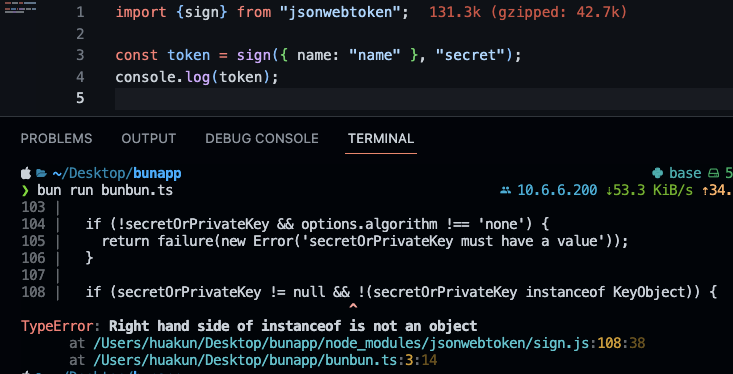
https://discord.com/channels/876711213126520882/887787428973281300/1073538772840480789
The text was updated successfully, but these errors were encountered: