New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Container Apps ingress returns "Bad Request" to Salesforce (works fine in App Service) #567
Comments
|
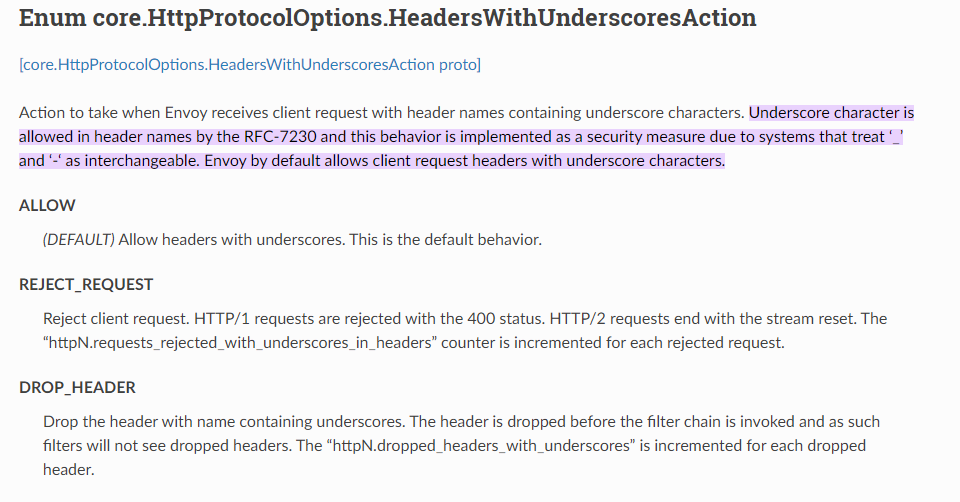
I have the same Bad Request error using custom http header parameters with an underscore _ in the name. e.g. |
|
Indeed salesforce does send a header with |
|
Relates to #264 |
|
I believe ACA uses Envoy as ingress; perhaps this setting is wrong? |
|
imho, I would suggest allowing header names with underscore, because, why not? I don't think that some legacy CGI system will be using container apps. |
|
Hi. We are working on a solution to this restriction. |
|
HI @anrub,@onionhammer, @SSilence . The fix is deployed in all regions. We are allowing header names with underscore. |
Should this issue be marked as closed then? |
This issue is a: (mark with an x)
Issue description
When issuing a new request from Salesforce, no matter which container is running, the request is stopped at ingress and responds with "Bad Request" and a status code of 400.
Steps to reproduce
or CURL:
curl -X GET -H "sfdc_stack_depth: 1" https://your-aca-endpoint.centralus.azurecontainerapps.ioExpected behavior [What you expected to happen.]
The container's http server should be invoked, allowing the container to handle the request
Actual behavior [What actually happened.]
Ingress stops the request and returns literal string "Bad Request" with status code of 400. The same container running on Azure App Service works fine via Salesforce
Screenshots

Bad request in debug output of salesforce
hello world running, works fine in browser and postman:

Additional context
Code to execute:
The text was updated successfully, but these errors were encountered: