-
Notifications
You must be signed in to change notification settings - Fork 2
New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
How to set up a Jenkins master node from scratch. #6
Comments
|
Adding Jenkins to systemd service: https://wiki.jenkins.io/display/JENKINS/Installing+Jenkins+as+a+Unix+daemon |
|
Maybe saving Jenkins configuration via: https://wiki.jenkins.io/display/JENKINS/JobConfigHistory+Plugin Or maybe you have better options. ;-) |
|
@trivialfis I believe Jenkins is already a system service in the Ubuntu environment; |
|
@trivialfis Very interesting. I'll check it out. All manual config is rather tedious. |
|
@hcho3 I see. Running |
|
@trivialfis This doc is now complete. Hope this helps you understand how the CI is set up. |
|
@hcho3 This is great! I will try to start with some simple tasks like upgrading the packages etc, so that I can learn to co-maintain it |
Eventually, I want to set up a script to set up a Jenkins master node automatically. Probably I'll want to set up a Dockerfile along with an entry script. But first I should document all steps.
The following sections describe all steps I took to set up a new Jenkins master node from scratch.
Launch an EC2 instance to host the Jenkins master
jenkins-master(opens 80/443 ports to the world);jenkins-ssh(opens port 22 to the world); andXGBoost-CI-Fleet(opens all ports to other EC2 instances in the same security group).ssh -i <private key> ubuntu@xgboost-ci.net. Note: we'll always use theubuntuuser when logging into the master node..ssh/authorized_keyfile. See this link for more details.Install system packages and set up Nginx + Jenkins
sudo apt-get update && sudo apt-get upgrade. Then reboot the machine (sudo reboot). Wait a while and re-establish the SSH connection.sudo apt-get install python3 python3-pip git. Install AWS CLI by runningpip3 install awscli.ubuntuuser to use Docker.i. Run
sudo ufw allow OpenSSHand thensudo ufw enable.ii. Then follow the instructions in How To Install Nginx on Ubuntu 18.04. Follow "Step 5 – Setting Up Server Blocks" as well.
sudo apt-get install openjdk-8-jdk-headless.jenkins-master. I will remove it once the reverse proxy is set up. Once you can access the web page http://xgboost-ci.net:8080 and follow the Jenkins setup wizard.i. Connect to master instance via SSH and run
sudo ufw delete allow 8080.ii. Go to the EC2 console and edit the security group
jenkins-masterto remove 8080 from the list of open ports.Configure Jenkins
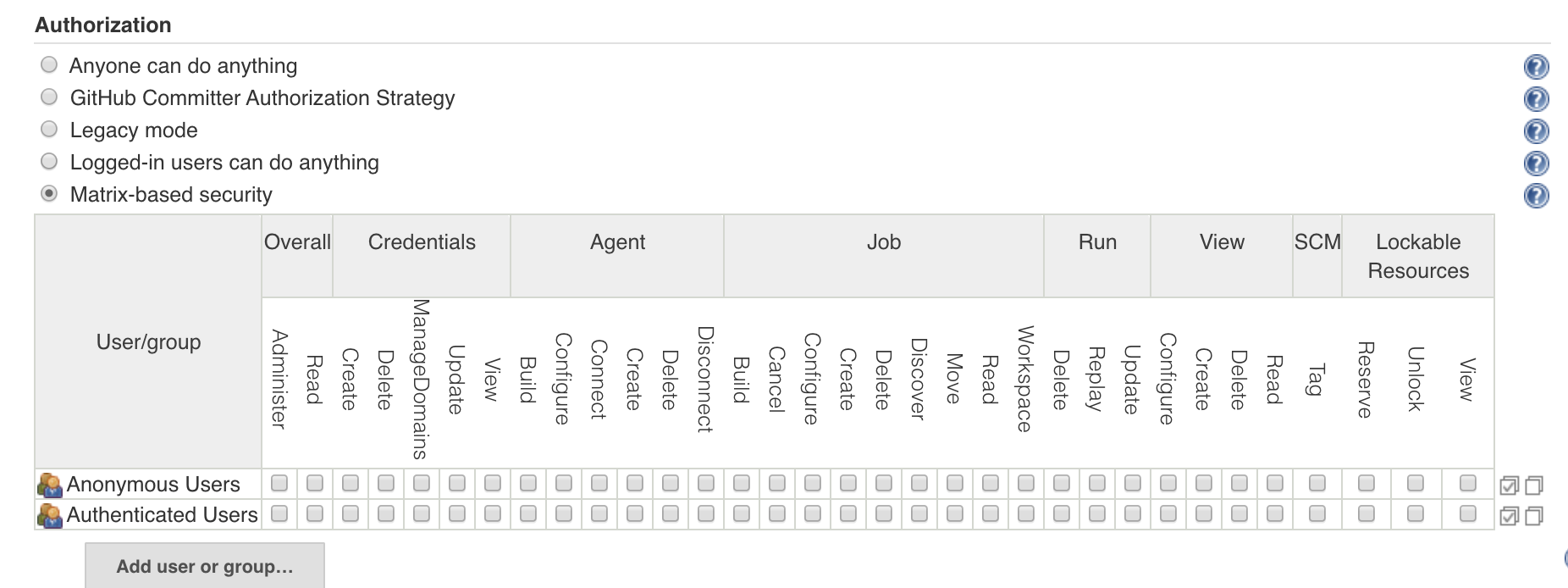
Click on the button "Add user or group..." and when prompted, enter the GitHub username. In my case, it's "hcho3". Since I am the admin, I will grant myself all permissions; for all others, grant read-only access.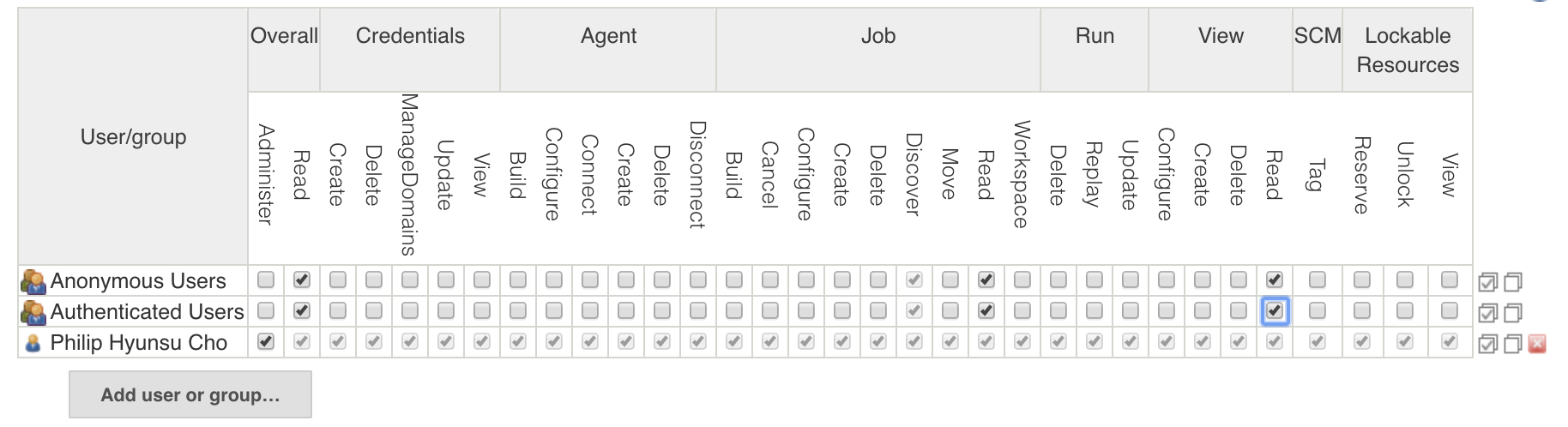
Note: collaborators will have be manually added to this matrix. For example:ubuntu.Navigate to Manage Jenkins > Configure System. Set "# of executors" to 0, since all jobs will be run in worker EC2 instances. The master-worker arrangement lets us run multiple test jobs simultaneously.
In the same page titled Configure System, fill out the form "GitHub Servers." This is needed to create a webhook to listen to GitHub events so that, e.g. every push event will trigger CI. For "Credentials," create a new personal access token with permissions admin:repo_hook, repo, and repo:status. Tick the checkbox "Manage hooks." Now save the configuration and refresh the page (Configure System). Then press the button "Re-register hooks for all jobs."
Set up IAM user for launching worker pool
See here if you need an introduction to the concept of IAM (Identity and Access Management). An IAM user is essentially a sub-account with restricted set of privileges.
XGBoost-CI-Workerswith the following set of permissions:Or use this JSON template:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "ec2:*" ], "Resource": "*" }, { "Effect": "Allow", "Action": [ "iam:ListRoles", "iam:PassRole", "iam:ListInstanceProfiles" ], "Resource": "*" } ] }XGBoost-CI-MasterandXGBoost-CI-Worker. Here are the list of policies to attach toXGBoost-CI-Master:{ "Version": "2012-10-17", "Statement": [ { "Sid": "VisualEditor0", "Effect": "Allow", "Action": "ecr:*", "Resource": "*" } ] }And assign the following policies to
XGBoost-CI-Workerrole:Then select Instance Settings > Attach/Replace IAM Role. In the next dialog page, choose
XGBoost-CI-MasterIAM role. Now the Jenkins master instance have all permissions that are associated with theXGBoost-CI-Masterrole. Super cool.xgboost-ci. Note that a pem file is downloaded. Do not lose it, as it is the only time you'll have access to the private key.Create AMIs (Amazon Machine Images) for workers
This section is glossing over many details. I hope to have an automatic script to automate AMI generation.
We need to create AMIs for the following targets:
For the Linux targets, it suffices to create a machine with Ubuntu 18.04 LTS and install Git, Python and Docker. (For GPU target, also install CUDA driver and nvidia-docker.) The use of Docker simplifies our job greatly, since all other package installation is abstracted into Dockerfiles. On the other hand, we can't use Docker on Windows targets, as nvidia-docker does not support Windows Docker. So we need to install all packages manually. Off of my head, they are:
xgboost-ci. (Mess this up, and the Jenkins master won't be able to SSH into the Windows workers.) Also pay attention to PubKey Auth not working PowerShell/Win32-OpenSSH#1306 (comment)See #7 for more details on setting up Windows machines.
Important: Make sure you registered the public key of the key pair
xgboost-ciin each Windows machine. Otherwise, Jenkins master will fail to establish connection with Windows workers.Register workers in Jenkins
TODO: want to implement a custom scaling logic in lieu of the EC2 plugin, since I've seen some failure modes before (dmlc/xgboost#4984 (comment))
us-west-2for Region. Now locate the private key (pem) file generated in Step 4 of the previous section and paste the content into the big text box titled "EC2 Key Pair's Private Key". Verify the setting by pressing the button "Test Connection".linux cpu(space in the middle)XGBoost-CI-WorkerIAM role, in the form ofarn:aws:iam::<AWS account ID>:instance-profile/XGBoost-CI-Worker)linux gpu(space in the middle)XGBoost-CI-WorkerIAM role, in the form ofarn:aws:iam::<AWS account ID>:instance-profile/XGBoost-CI-Worker)linux mgpu(space in the middle)XGBoost-CI-WorkerIAM role, in the form ofarn:aws:iam::<AWS account ID>:instance-profile/XGBoost-CI-Worker)win64 build(space in the middle)C:\\Windows\\Temp<- Don't forget this, otherwise Windows worker won't launchXGBoost-CI-WorkerIAM role, in the form ofarn:aws:iam::<AWS account ID>:instance-profile/XGBoost-CI-Worker)win64 cpu(space in the middle)C:\\Windows\\Temp<- Don't forget this, otherwise Windows worker won't launchXGBoost-CI-WorkerIAM role, in the form ofarn:aws:iam::<AWS account ID>:instance-profile/XGBoost-CI-Worker)win64 gpu cuda9(spaces in between)C:\\Windows\\Temp<- Don't forget this, otherwise Windows worker won't launchXGBoost-CI-WorkerIAM role, in the form ofarn:aws:iam::<AWS account ID>:instance-profile/XGBoost-CI-Worker)win64 gpu cuda10_0(spaces in between)C:\\Windows\\Temp<- Don't forget this, otherwise Windows worker won't launchXGBoost-CI-WorkerIAM role, in the form ofarn:aws:iam::<AWS account ID>:instance-profile/XGBoost-CI-Worker)win64 gpu cuda10_1(spaces in between)C:\\Windows\\Temp<- Don't forget this, otherwise Windows worker won't launchXGBoost-CI-WorkerIAM role, in the form ofarn:aws:iam::<AWS account ID>:instance-profile/XGBoost-CI-Worker)Add XGBoost repo to Jenkins via the Blue Ocean interface.
master release_* PR-*.Also add behavior "Filter pull requests by commit message", which will skip CI for any pull request whose last commit's message contains the phrase
[skip ci].Save the configuration. Upon saving, Jenkins will scan the repository and find all branches and pull requests that are eligible for building and testing. So far, we've excluded any branch that is neither master or a release.
4. Now install the AnsiColor plugin to enable colored consoled output. This also fixes all failing tests. Then run "Scan repository now" to create build jobs for all branches and currently open pull requests.
Set up pipeline for Windows targets
Currently, we set up a separate testing pipeline for Windows targets. The pipeline configuration is stored in Jenkinsfile-win64.
Access the classical interface of Jenkins by visiting https://xgboost-ci.net. Then on the left sidebase, click "New Item." (If you don't see this, make sure to log in first.)
Create
xgboost-win64pipeline by copying fromxgboostpipeline:Jenkinsfile-win64.The text was updated successfully, but these errors were encountered: