New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Disable loading external DTDs by default, create system property to activate it #6474
Labels
Milestone
Comments
romani
added a commit
that referenced
this issue
Feb 24, 2019
romani
added a commit
that referenced
this issue
Feb 25, 2019
|
without new system property checkstyle might failure the same way as failed our UTs: |
This was referenced Feb 25, 2019
|
fix is merged and released in 8.18 |
1 task
Fokko
added a commit
to Fokko/spark
that referenced
this issue
Aug 13, 2019
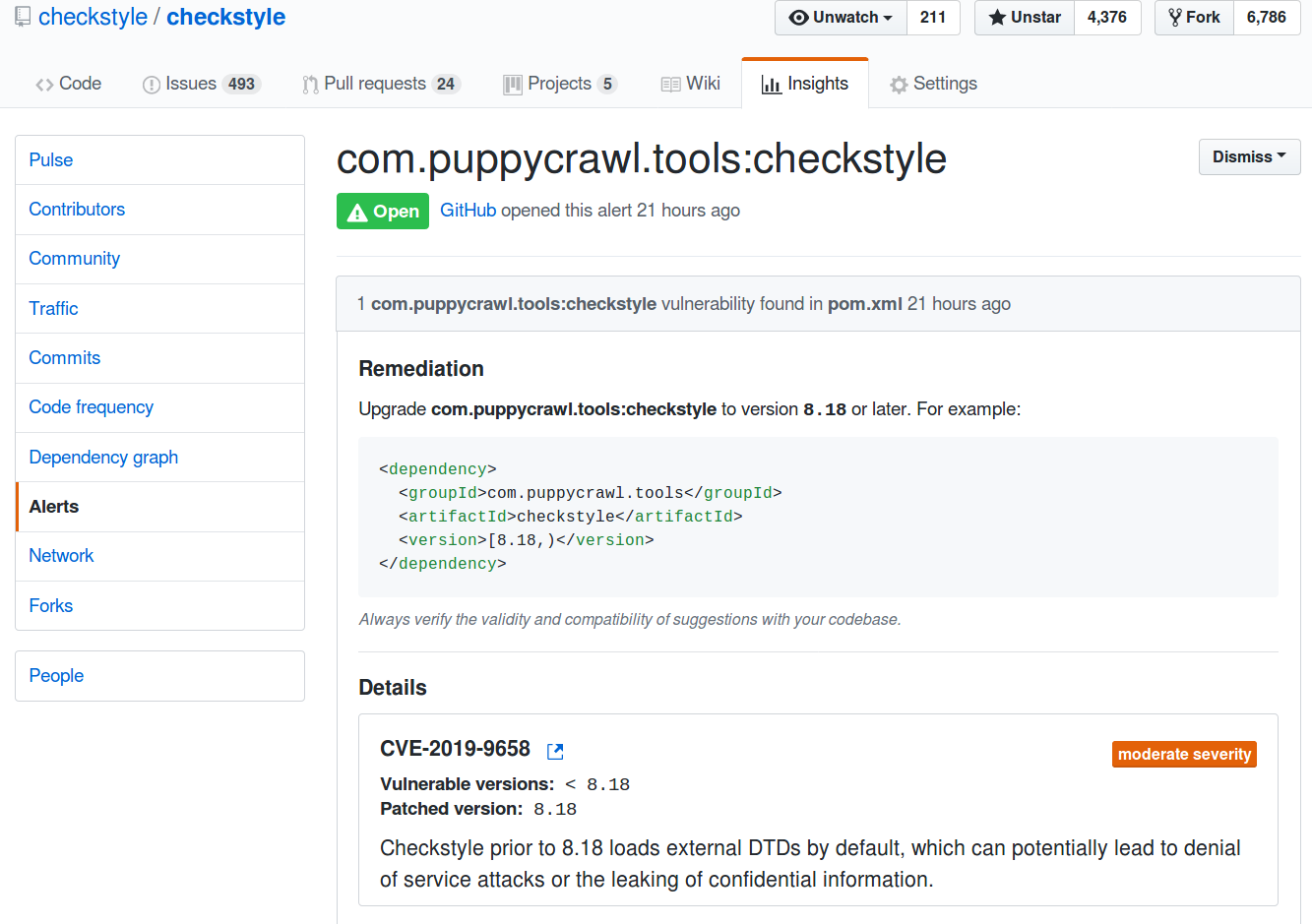
Fixes a vulnerability from the GitHub Security Advisory Database: _Moderate severity vulnerability that affects com.puppycrawl.tools:checkstyle_ Checkstyle prior to 8.18 loads external DTDs by default, which can potentially lead to denial of service attacks or the leaking of confidential information. checkstyle/checkstyle#6474 Affected versions: < 8.18 Ran checkstyle locally. Closes apache#25432 from Fokko/SPARK-28713. Authored-by: Fokko Driesprong <fokko@apache.org> Signed-off-by: Dongjoon Hyun <dhyun@apple.com> (cherry picked from commit d8dd571)
dongjoon-hyun
pushed a commit
to apache/spark
that referenced
this issue
Aug 13, 2019
## What changes were proposed in this pull request? Backport to `branch-2.4` of #25432 Fixes a vulnerability from the GitHub Security Advisory Database: _Moderate severity vulnerability that affects com.puppycrawl.tools:checkstyle_ Checkstyle prior to 8.18 loads external DTDs by default, which can potentially lead to denial of service attacks or the leaking of confidential information. checkstyle/checkstyle#6474 Affected versions: < 8.18 ## How was this patch tested? Ran checkstyle locally. Closes #25437 from Fokko/branch-2.4. Authored-by: Fokko Driesprong <fokko@apache.org> Signed-off-by: Dongjoon Hyun <dhyun@apple.com>
rluta
pushed a commit
to rluta/spark
that referenced
this issue
Sep 17, 2019
## What changes were proposed in this pull request? Backport to `branch-2.4` of apache#25432 Fixes a vulnerability from the GitHub Security Advisory Database: _Moderate severity vulnerability that affects com.puppycrawl.tools:checkstyle_ Checkstyle prior to 8.18 loads external DTDs by default, which can potentially lead to denial of service attacks or the leaking of confidential information. checkstyle/checkstyle#6474 Affected versions: < 8.18 ## How was this patch tested? Ran checkstyle locally. Closes apache#25437 from Fokko/branch-2.4. Authored-by: Fokko Driesprong <fokko@apache.org> Signed-off-by: Dongjoon Hyun <dhyun@apple.com>
kai-chi
pushed a commit
to kai-chi/spark
that referenced
this issue
Sep 26, 2019
## What changes were proposed in this pull request? Backport to `branch-2.4` of apache#25432 Fixes a vulnerability from the GitHub Security Advisory Database: _Moderate severity vulnerability that affects com.puppycrawl.tools:checkstyle_ Checkstyle prior to 8.18 loads external DTDs by default, which can potentially lead to denial of service attacks or the leaking of confidential information. checkstyle/checkstyle#6474 Affected versions: < 8.18 ## How was this patch tested? Ran checkstyle locally. Closes apache#25437 from Fokko/branch-2.4. Authored-by: Fokko Driesprong <fokko@apache.org> Signed-off-by: Dongjoon Hyun <dhyun@apple.com>
1 task
Sign up for free
to join this conversation on GitHub.
Already have an account?
Sign in to comment
Ability to load external DTDs is considered as security issue, especially if DTDs are not hosted on
httpshosting.Checkstyle used to rely on remote DTD files previously so such ability was enabled by default.
From 8.11 version checkstyle do not rely on remove DTDs if you use standard config, with standard DTDs.
UPGRADE INSTRUCTIONS: Users still can activate not very secure behavior by system property
checkstyle.enableExternalDtdLoad, so simply make your CLI execution likejava -Dcheckstyle.enableExternalDtdLoad=true -jar .......Or activate system property by any other way in your checkstyle execution.
ATTENTION: user on old versions of checkstyle that reference to DTD files
http(not secure) hosting on sourceforge.net will be forced to upgrade to at least tohttpsversions of DTD files. Removal of DTDs onhttphosting will be done in scope of - #6478.The text was updated successfully, but these errors were encountered: