New issue
Have a question about this project? Sign up for a free GitHub account to open an issue and contact its maintainers and the community.
By clicking “Sign up for GitHub”, you agree to our terms of service and privacy statement. We’ll occasionally send you account related emails.
Already on GitHub? Sign in to your account
Bug version 0.28.1: IReader.MoveToNextEntry() is not working with encrypted zip files #584
Comments
|
I think I'm experiencing this issue too. I thought it was #514 so I posted my findings there: #514 (comment) |
|
This is weird because I have a test that literally tests this. If you could post a sample file, that would be helpful. Here's the test: |
|
I think I have found the constellation where the error occurs: |
|
I can confirm that zipping the same collection of files with ZipCrypto vs AES-256 and running that unit test does replicate the issue on my side too (i.e. only one file extracted when ZipCrypto, totally fine with AES-256). Further to that, the I'm guessing some zip tools, namely some versions of Windows, might still use ZipCrypto as the default despite its weakness? Here are my test zip files, both with password "test". Hope it helps. (Note that you can easily create both types of zip files using 7-zip file manager) |
|
Found the issue which was because of a recent change and fixed it: #593 |
|
fix released in 0.28.2 |
|
I'm still facing this problem with 0.32.2, AES256-encrypted zip files are fine but not ZipCrypto-encrypted. |
|
Odd. The test explicitly tests that. I wonder if I have some type issues so it's still using the Span method |
I'm using SharpCompress in an UWP project, does it matter? The ZipCrypto arichive is created by Bandizip with default setting. |
|
UWP is slightly different than other other environments. I'll take a closer look but I'd also see if your code can decrypt the file on the regular .NET runtime. |
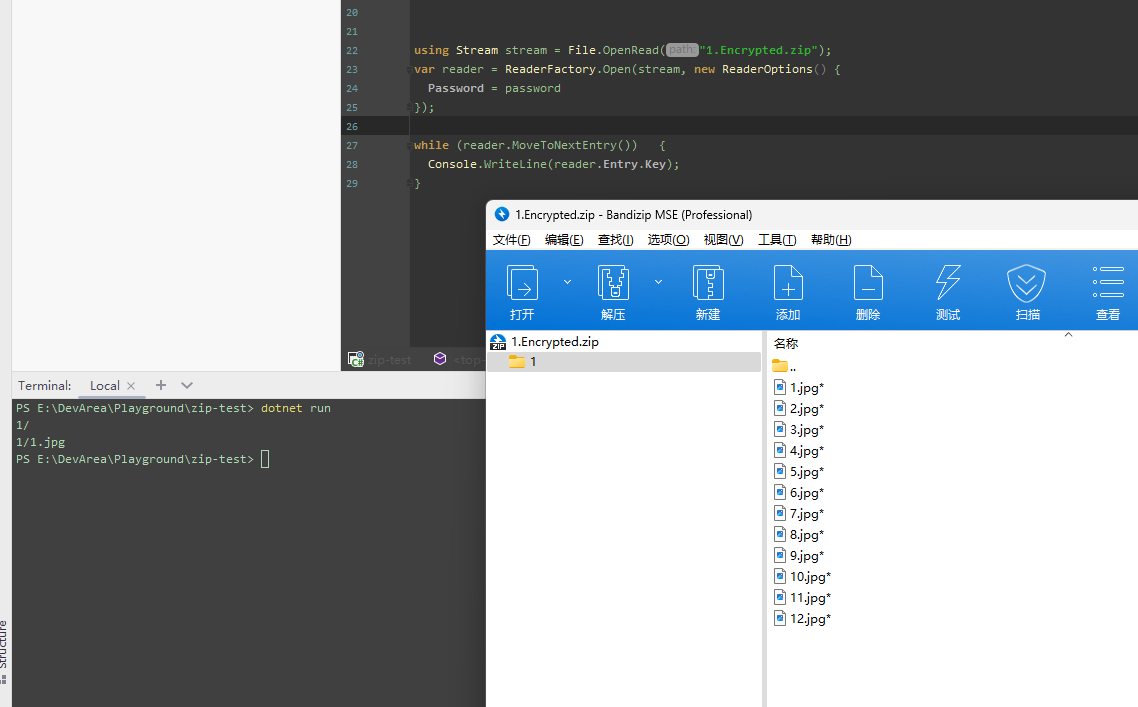
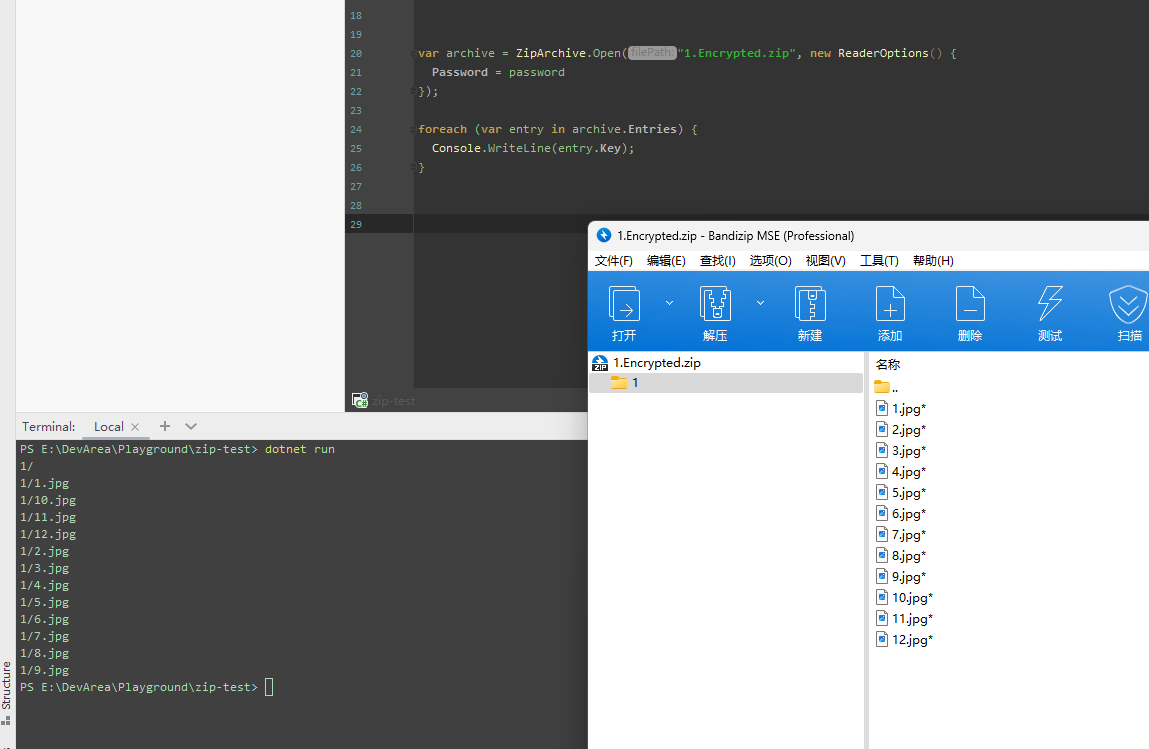
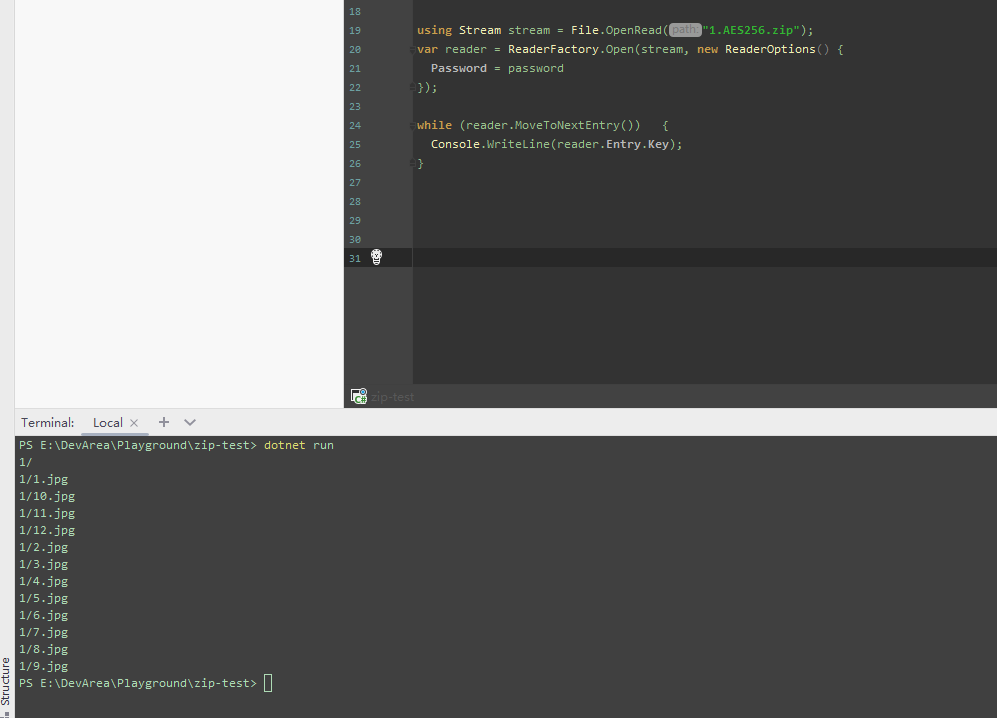
I've created a .NET 7 console app and it turned out Reader API doesn't work properly: with Archive API: PS: What's going on with AES256 one: |
|
Still should be the same as Any chance of sharing the file? Is it this specific one or all? |
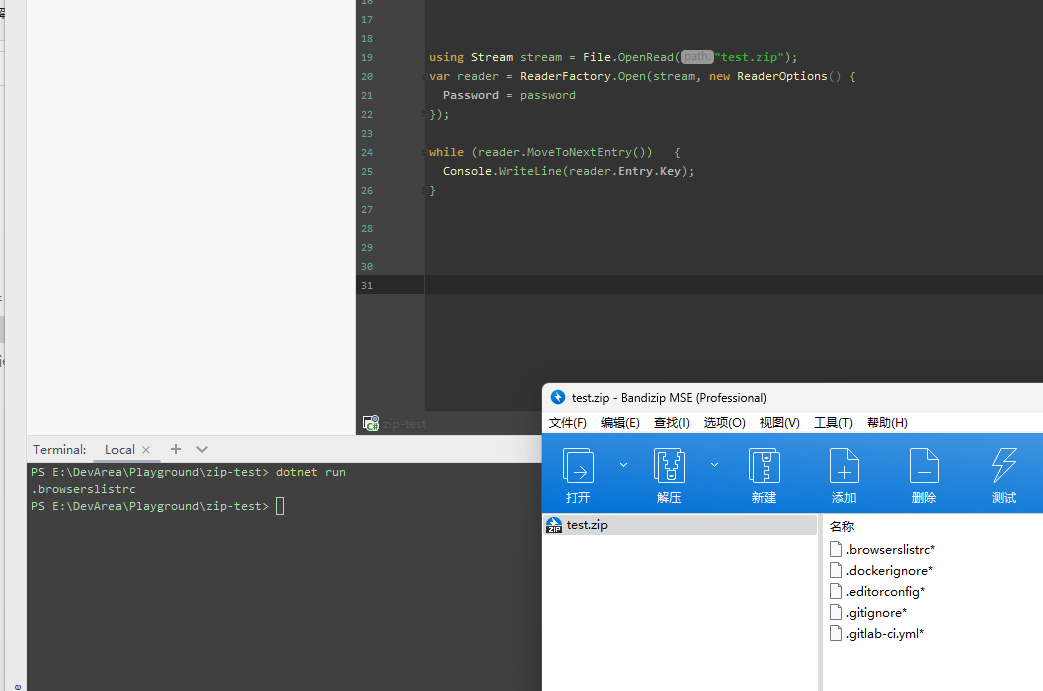
Sure, the ZipCrypto one is here: 1.ZipCrypto.zip Every single archive I've created using Bandizip with ZipCrypto encryption doesn't work properly, like: |
|
Actually, I think Bandizip is creating bad Zip files. All the entries are flagged as having a post data descripter header even though they do not. You can see the Flags of headers having Archive API works because it uses the dictionary at the end of the file to seek to the entries instead of streaming through the file. |
Indeed. I didn't see there was a Thanks for your hard work, maybe I have to send Bandizip an email. |
|
Hello. I'm a developer of Bandizip. It's an Info-zip's modification of bit3. I made a sample zip file with the same problem using this command-line in Ubuntu. zip -e -X infozip.zip a.txt b.txt This is the comment for the bit3 in 7zip source. |
|
that totally breaks streaming zip reading: |
|
I know it's weird. I was confused too when I faced a sample of such type. Info-zip's modification has an advantage when you create an encrypted ZIP file. For example, make a big file ( fsutil file createnew bigfile 100000000000 ) and So, the modification is suitable to create streaming ZIP. |
|
@kippler what do you do for streaming zips altogether then? Or does Bandi-zip just not care about the trailer for streaming zips at all? I'm not sure what to do here. You could say "Reader with Encrypted" isn't supported or add a custom option for these use cases. It's really silly that info-zip modified an existing, well documented bit flag. |
|
In most cases, Bandizip checks the central header instead of the local header. Bandizip opens ZIP in streaming mode only when the central header is broken, and here is the rule I use. bit0:0 bit3:1 -> Data descriptor exists. I agree with you. It's so silly, but what can I do? |
|
I'll look into implementing the above. Been out of it for personal reasons. |
|
I still experience this issue, version 0.35.0 |
In Version 0.27.1 IReader.MoveToNextEntry() was working well with encrypted zip files
When project is updated to 0.28.1, the method is only working once and is returning false after first file has been extracted.
The problem seems to be with encrypted zip files only:
Example:
`using Stream stream = File.OpenRead(@"C:\Temp\SharpCompressTest\SharpCompressTest.zip");
var reader = ReaderFactory.Open(stream, new ReaderOptions { Password = "1234" });
// Version 0.28.1: While loop will only extract first file instead of all files
while (reader.MoveToNextEntry())
{
reader.WriteEntryToDirectory(@"C:\Temp\SharpCompressTest", new ExtractionOptions()
{
ExtractFullPath = true,
PreserveFileTime = true
});
}`
The text was updated successfully, but these errors were encountered: